Building Blocks for Zero Trust Architecture
Essential Elements for Building ZTA
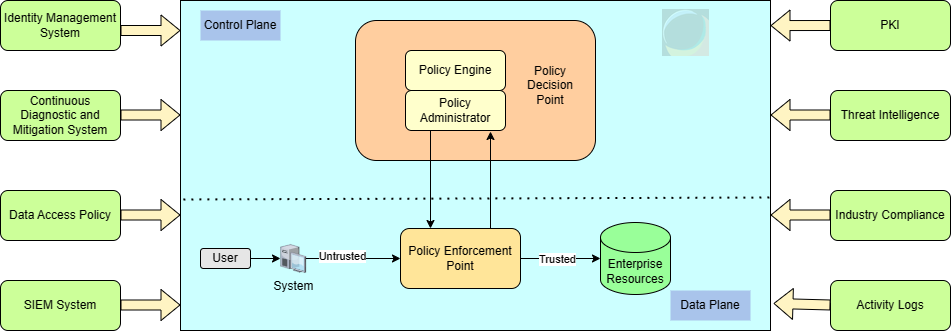
In my last post, we explored the core design principles of Zero Trust Architecture (ZTA). Building on that foundational knowledge, let's now delve into the building blocks of ZTA. For a visual guide, refer to the attached schematic, which outlines a simplified view of ZTA's components.
A crucial aspect to understand before diving into individual components is the segregation of the Control and Data planes in ZTA. Consider the Control plane as a traffic control system, determining the flow of data like traffic lights guide cars. In contrast, the Data plane is like the roads and highways, where the actual data movement (like cars on a road) occurs.
Key Components of ZTA:
Policy Engine: This is the heart of the decision-making process, determining access based on enterprise policy and inputs from systems like Continuous Diagnostic and Management System and Identity Management System. These inputs feed into a trust algorithm, which helps grant, deny, or revoke access.
Policy Administrator: Responsible for establishing and terminating communication paths between a subject and a resource. It also provides session-specific authentication and authorization tokens.
Policy Enforcement Point (PEP): PEP works in tandem with the Policy Administrator, applying the policy decisions. It's a pivotal point in managing, enabling, and terminating sessions between a client and a resource. PEP can be further divided into two parts: the client side (an agent on an endpoint) and the resource side (a gateway controlling access).
In addition to these core components, several other elements support the policy engine in making informed access decisions. I will cover these important data sources in my next post.
You can try mapping these components to any vendor provided ZTA solution, where you'll find similar structures such as a policy engine for configuring access and gateways delineating trust zones.
I've kept this overview concise to ensure clarity and engagement. How do you see these components integrating into your cybersecurity strategies? I'm excited to hear your thoughts and experiences!
Stay tuned for more in-depth discussions in future posts.
Disclaimer: The views and opinions expressed in this post are solely my own and do not reflect the official policy or position of my employer.